Introduction : CNDP Hack
The National Control Commission for the Protection of Personal Data (CNDP), a key Moroccan institution responsible for data privacy, recently fell victim to the Japanese Keyword Hack—a well-known attack that hijacks a website’s Google search results, replacing its indexed pages with Japanese text promoting fake products.

This type of attack is most common on WordPress websites that have security weaknesses, often due to cracked (nulled) themes and plugins or outdated software.
In this article, we’ll break down exactly how this attack happens, why it’s dangerous, and how you can protect your website from suffering the same fate.
What is the Japanese Keyword Hack?
The Japanese Keyword Hack (also known as the Japanese SEO Spam Attack) is a search engine poisoning technique. Hackers inject malicious code into a website to generate thousands of Japanese spam pages, which then appear in Google search results.
These fake pages promote counterfeit products, scams, or even phishing websites—damaging the original website’s SEO ranking, reputation, and credibility.
How Do You Know If a Website is Infected?
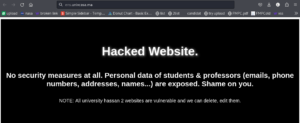
A hacked website may look perfectly normal when visited directly, but in Google search results, its indexed pages appear in Japanese text.
How Did the CNDP Hack Happen?
The CNDP website appears to be using WordPress site:
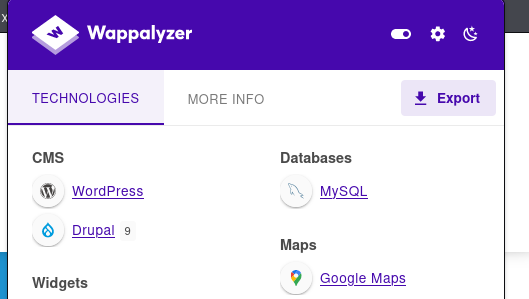
Since this type of attack typically targets WordPress sites, here’s how the hackers likely took control:
1. Installation of a Backdoor
Hackers exploit vulnerabilities in:
- Nulled (cracked) themes and plugins – These come with hidden malware.
- Outdated WordPress versions – Older versions have known security flaws.
- Weak credentials – Attackers brute-force login credentials.
Once inside, they inject a PHP backdoor (a hidden malicious file) that allows them to execute commands and modify the website remotely.
2. Modifying the Database
The attacker adds fake posts and pages in the WordPress database, filling them with Japanese text and inserting SEO keywords for ranking. These pages are usually hidden from normal visitors but visible to Googlebot.
🔍 How they hide it:
- They insert obfuscated PHP scripts that generate spam dynamically.
- They manipulate the database by adding new posts in
wp_posts. - They modify the
wp_optionstable to create redirects or store backdoors.
3. Injecting Malicious Scripts
To ensure persistence and hide their tracks, hackers modify:
✅ .htaccess file – To redirect Googlebot while showing normal users the correct website.
✅ wp-config.php – To create hidden users or backdoors.
✅ Themes and plugin files – To reinfect the site even if the owner removes some files.
4. Hijacking Google Search Results
Since Google sees only the spam pages (not the original content), it replaces the site’s actual pages with the hacker’s injected pages.
This is why when searching for the CNDP website, visitors see Japanese product listings instead of official content.
💡 Key Sign of Infection:
- Google Search results show Japanese text instead of the actual site content.
- The website is flagged as hacked in Google Search Console.
- Clicking on the fake pages redirects users to other scam sites.
- New admin users might appear in the WordPress dashboard.
How to Fix & Prevent the Japanese Keyword Hack
If your WordPress site is hacked with this type of malware, take immediate action:
✅ 1. Scan Your Site for Malware
Use security plugins like:
- Secureweb Scanner
- Wordfence Security
- Sucuri Security
These will help detect backdoors and malware infections.
✅ 2. Check and Clean Your Database
- Go to phpMyAdmin in your hosting panel.
- Look at
wp_posts,wp_options, andwp_terms.
✅ 3. Remove Malicious Files
- Check wp-content/themes/ and wp-content/plugins/ for strange files.
- Delete all unused themes and plugins.
- If you find unknown PHP files, delete them immediately.
✅ 4. Reset .htaccess & wp-config.php
- Hackers often modify the
.htaccessfile to redirect search engines. - Check for strange lines like
Redirect 301orRewriteRulesending traffic elsewhere.
To fix it, reset .htaccess: Go to File Manager (or FTP), Locate .htaccess in public_html and replace its content with WordPress’s default .htaccess file found here. (Backup your actual .htaccess code)
✅ 5. Remove Hidden Admin Users
- In WordPress, go to Users → All Users.
- If you see unknown admin accounts, delete them.
✅ 6. Reinstall WordPress Core Files
- Download a fresh copy of WordPress.
- Replace everything except
wp-contentandwp-config.php.
✅ 7. Secure Your Website
Now that you’ve removed the malware, you must harden security:
- Enable two-factor authentication (2FA).
- Use a security plugin like Wordfence or iThemes Security.
- Disable file editing (
define('DISALLOW_FILE_EDIT', true);inwp-config.php). - Keep everything updated – WordPress, themes, and plugins.
- Use strong passwords and limit login attempts.
Conclusion: Don’t Play it Smart with Nulled Themes & Plugins 🚨
Many website owners think they’re saving money by downloading nulled (pirated) themes and plugins. But these free downloads come with malware, hidden backdoors, and SEO spam that can destroy their entire business.
👉 The lesson from the CNDP Hack: If you try to be “smart” and save money on security, you’ll end up paying way more when hackers take over your website.
💡 Instead, always:
✔ Use official, regularly updated plugins and themes.
✔ Install a security plugin like Wordfence, MalCare, or iThemes Security.
✔ Regularly scan your website and keep daily backups.
If you think your website has been hacked by the Japanese Keyword Hack, contact us now for a free malware scan and website security audit.