If you’re a developer, the security of your application is your responsibility. One of the most common, yet dangerous, vulnerabilities you might face is called IDOR, or Insecure Direct Object Reference. The good news? Learning how to Fix IDOR is straightforward once you understand the core problem.
In this guide, we’ll break down IDOR in simple terms. You’ll learn what it is, see how attackers exploit it, and, most importantly, discover the proven strategies to Fix IDOR vulnerabilities in your code for good.
What Exactly is an IDOR Vulnerability? Let’s Simplify.
Imagine a bank where your account number is also the key to your safety deposit box. If someone knows your account number, they can simply walk up and try to open your box. An IDOR vulnerability is the digital version of this flaw.
In technical terms, IDOR occurs when a web application exposes a direct reference to an internal object, like a file, database record, or account. An attacker can then manipulate this reference to access data they are not authorized to see.
A Classic IDOR Example Everyone Can Understand
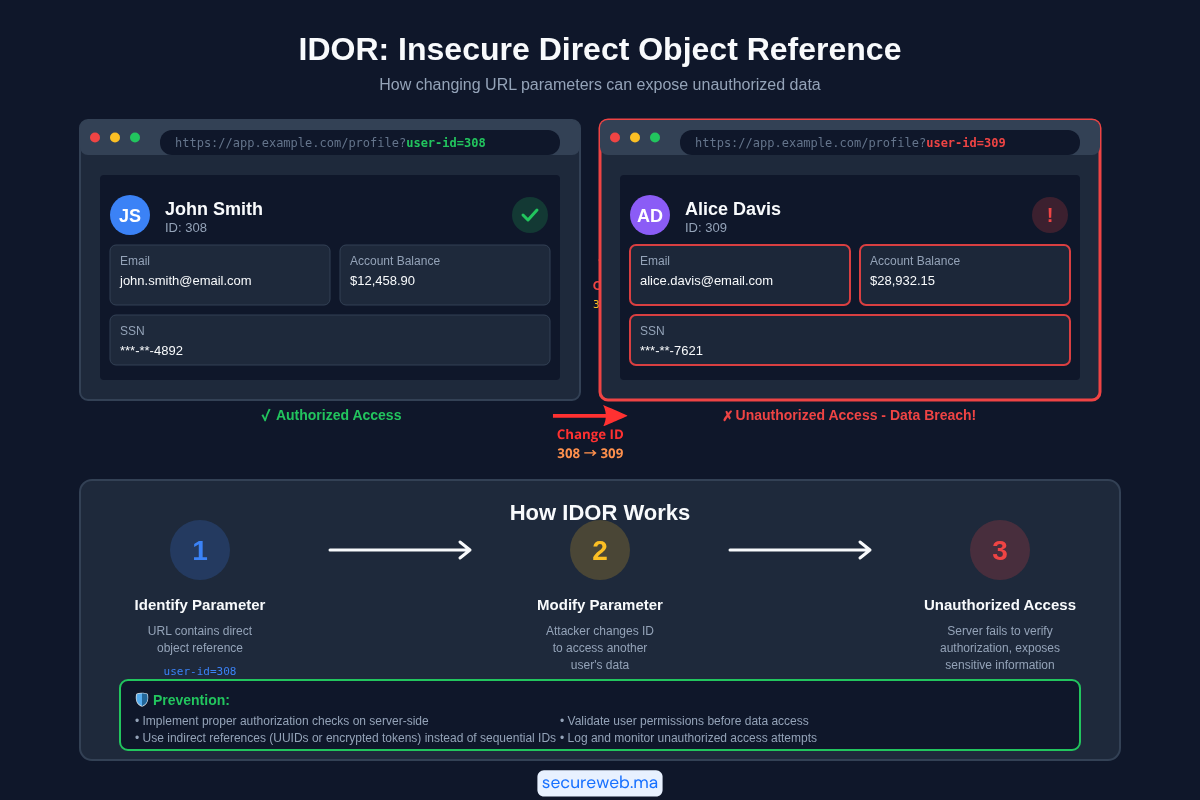
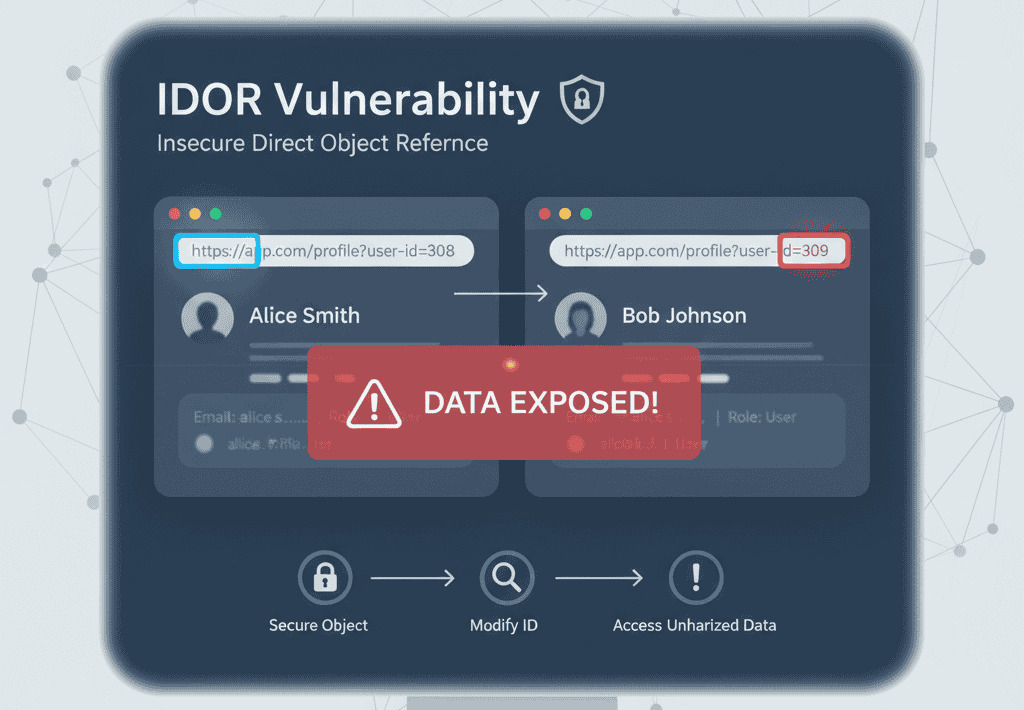
Let’s say you’re on a social media site. Your profile URL looks like this:https://example.com/profile?user_id=123
When you visit this URL, you see your profile. The number 123 is your user ID in the database. Now, what happens if you change the URL to ...user_id=124?
- If you see another user’s private profile: Congratulations, you’ve found an IDOR bug! The application showed you data you shouldn’t have access to because it trusted the user-supplied ID (
124) without verifying if you had permission. - If you get an “Access Denied” error: The application did its job correctly. It checked your permissions and blocked the request.
How Do Hackers Exploit IDOR? It’s Easier Than You Think.
Exploiting an IDOR doesn’t require advanced tools; it often just requires a curious mind and changing a number in the address bar. This is called “parameter tampering.”
But it’s not just about URLs. IDOR can lurk in many places:
- API Endpoints:
GET /api/orders/1001 - Form Fields:
<input type="hidden" name="document_id" value="554"> - File Paths:
https://site.com/download?file=invoice_789.pdf
Attackers don’t just guess IDs at random. They use automated scripts to scan thousands of numbers quickly, a process known as “enumeration.” This can lead to massive data breaches.
How to Fix IDOR: The Golden Rule of Access Control
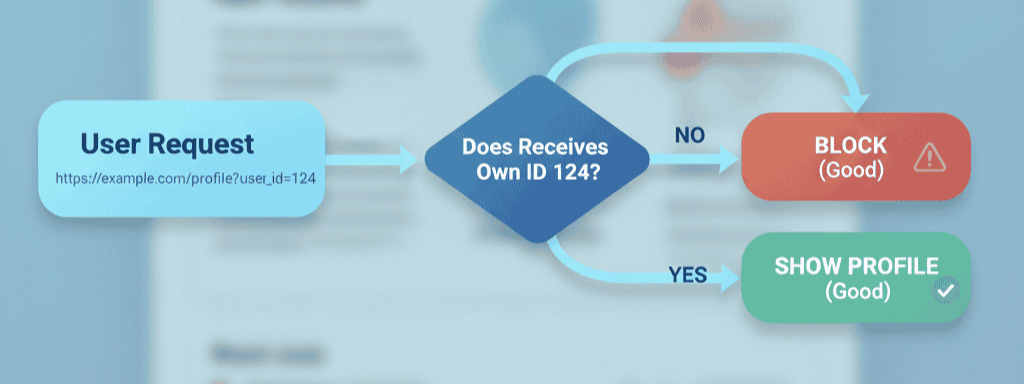
The root cause of an IDOR is a failure to check authorization. The application authenticates who you are (you are logged in) but fails to authorize what you are allowed to do (you can only see your own data).
To Fix IDOR, you must enforce the principle: “Never trust user-provided references. Always verify access on the server.”
Here are the most effective strategies to implement this.
Strategy 1: Implement Access Control Checks (The Most Important Fix)
This is the fundamental solution. For every request involving a sensitive object, your server-side code must ask: “Is the currently logged-in user allowed to access this specific object?”
Let’s look at vulnerable code and how to fix it.
Vulnerable Code (Python/Flask Example):
@app.route('/api/orders/')
def get_order(order_id):
# DANGER: This directly uses the user-provided order_id without any check!
order = db.get_order(order_id)
return jsonify(order)
Fixed Code (With Access Control):
@app.route('/api/orders/')
def get_order(order_id):
# DANGER: This directly uses the user-provided order_id without any check!
order = db.get_order(order_id)
return jsonify(order)
This simple check —order.user_id == current_user_id— is what fixes the IDOR vulnerability.
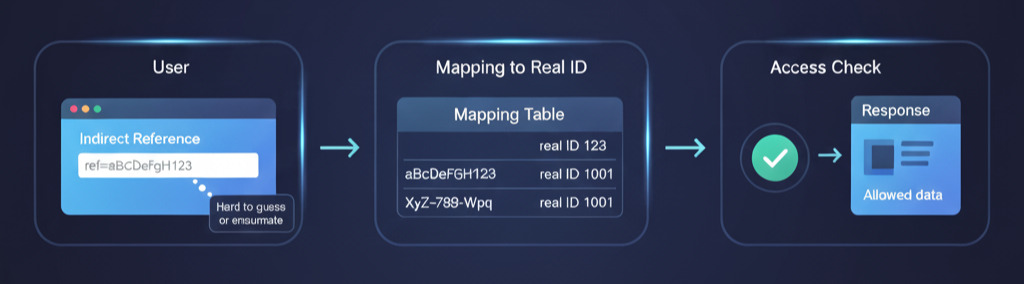
Strategy 2: Use Indirect Object References
Instead of exposing real database keys (like user_id=123), you can map them to random, unpredictable values.
- Real ID:
123-> Indirect Reference:aBcDeFgH123 - Real ID:
1001-> Indirect Reference:XyZ-789-Wpq
The server maintains a mapping table to translate the indirect reference back to the real ID. This makes it much harder for an attacker to guess or enumerate valid references.
Strategy 3: Use UUIDs Instead of Sequential IDs
If you can’t use indirect references, avoid using simple integers (1, 2, 3…) as keys for sensitive data. Instead, use Universally Unique Identifiers (UUIDs).
- Sequential ID (BAD):
invoice_id=1001 - UUID (GOOD):
invoice_id=550e8400-e29b-41d4-a716-446655440000
UUIDs are random and astronomically hard to guess, which effectively prevents enumeration attacks.
Best Practices to Permanently Fix IDOR in Your Workflow
- Code Review is Key: During peer review, always ask, “Where did this ID come from, and is there an access check for it?”
- Penetration Testing: It’s difficult to find every vulnerability in your own application. A professional penetration test simulates real-world attacks to find and fix critical bugs like IDOR before attackers can exploit them. [Contact us today] to learn how our security testing services can help you secure your application.
- Leverage Frameworks: Use built-in access control features in your web framework (e.g., Django’s permission classes, Spring Security in Java) rather than building everything from scratch.
- Adopt a “Zero-Trust” Mindset: The default stance should be to deny all access. Grant access only after an explicit, successful authorization check.
Conclusion
Fixing IDOR is not about using a magic library; it’s about adopting a secure mindset. The vulnerability stems from a simple missing check, but the consequences can be catastrophic, leading to massive data leaks.
By understanding that you must never trust user-provided references and always enforce server-side access control, you can effectively Fix IDOR and build applications that are secure, trustworthy, and resilient against one of the web’s most common attacks.
Have you ever found or fix IDOR bug? Share your story in the comments below!





