HTML Injection bug in NASA Auto-Reply Email
Author: Amine SAJID
Introduction
Hey hackers, today I’m going to share an exciting story about how I uncovered a bug in NASA that allowed me to inject HTML content into their auto-reply emails. This vulnerability could have been exploited for phishing attacks, malicious link injection, or even social engineering exploits. Let’s dive into the details!
Bug Type: HTML Injection (Email Auto-Reply)
Impact: Phishing, HTML Content Injection
Severity: Medium
The Hunt Begins: Finding the Bug in NASA
It all started with some good old-fashioned Google dorking. After a bit of searching, I stumbled upon a fresh NASA subdomain: https://redacted.nasa.gov. My curiosity was piqued, and I decided to dig deeper.
The subdomain hosted a registration page with standard input fields: First Name, Last Name, and Email Address. I filled out the form with dummy data and hit submit. Moments later, I received a welcome email from NASA. The email looked something like this:
Dear {First Name},
Welcome to NASA! You now have access to…
The Lightbulb Moment: Testing for HTML Injection
I noticed that the {First Name} field in the email was directly reflecting the input I had provided during registration. This got me thinking: What if I inject some HTML code into the First Name field?
I quickly signed up again, but this time, I entered the following payload into the First Name field:
<a href="https://secureweb.ma">POC</a>
Then, I submitted the form with a valid email address.
To my surprise, the auto-reply email from NASA rendered the HTML tags instead of treating them as plain text! The email now contained a clickable link, proving that the system was vulnerable to HTML injection.
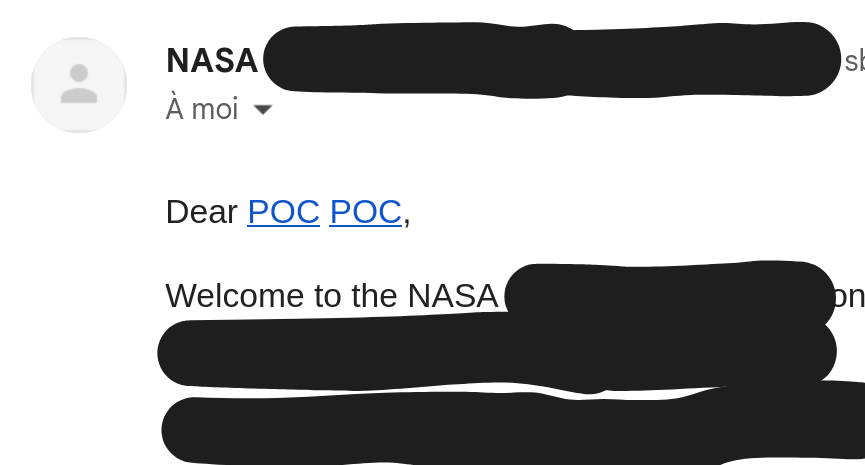
The Impact: Why This Bug in NASA Matters
While HTML injection might not seem as critical as XSS, it still poses significant risks:
- Phishing Attacks: An attacker could inject malicious links or fake login pages, tricking users into revealing sensitive information.
- Brand Reputation Damage: Imagine offensive or misleading content being injected into NASA’s emails—this could severely harm their credibility.
The Fix: How NASA Can Patch This Bug
To prevent such vulnerabilities, NASA should implement proper input validation and encoding. Here’s what they can do:
- Sanitize User Inputs: Strip out or escape HTML special characters (
< > " ' &) before processing or storing user data. - Use Built-in Functions: Leverage functions like
htmlspecialchars()in PHP or equivalent methods in other programming languages.
Conclusion:
This discovery underscores the importance of sanitizing user input, especially when reflecting user-controlled data in emails or notifications. Even seemingly minor vulnerabilities like this can have serious consequences if left unaddressed.
After responsibly reporting this bug in NASA, they sent me this letter of appreciation: 🚀
Final Thoughts
Finding this bug in NASA was both thrilling and eye-opening. It’s a reminder that no system, no matter how advanced, is immune to vulnerabilities. As hackers, it’s our responsibility to uncover these flaws and help organizations strengthen their defenses.