How My First Bug Turned into a Bounty
Author: Amine SAJID
Introduction
During a security assessment of a private program, I discovered an information disclosure that allows attackers to access sensitive information of 427 user (Payment preferences, personal info…)
Bug Type: Information Disclosure
Severity: Medium
The Hunt Begins
I got invited to a new private program, and the scope was: target.com, so subdomains were not in scope. I started hunting on the main domain and noticed that it interacted with a subdomain—let’s call it media.target.com. A quick search on the Wayback Machine (Archive) revealed a lot of PDF files named like 22434.pdf, 72452.pdf, and so on. These files contained payment receipts, which included sensitive information such as national identity numbers, names, addresses, phone numbers, and more.
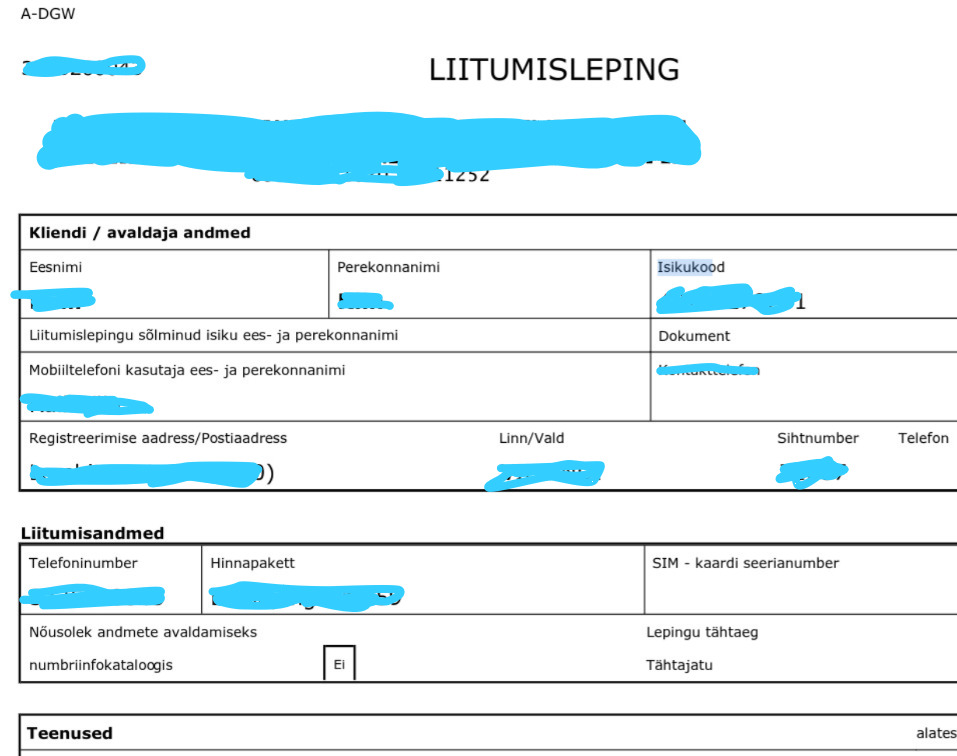
I reported the bug, and it was accepted even though the subdomain wasn’t in scope. I received my bounty within a day.
Impact
Unauthorized access to user’s private information.
Recommended Fix
Move the PDF files to a secure private folder
Conclusion
This experience taught me that hunting out-of-scope bugs can still be effective, especially when they impact the main domain’s users. Additionally, out-of-scope targets are often overlooked by hackers, making it easier to uncover critical vulnerabilities. I reported the issue and earned a bounty, proving the value of exploring beyond the defined scope.
Final Thoughts:
The first bug has a special feeling, especially when you find it in a bug bounty program and get your effort paid off.