Simple 2FA Bypass Bug Allowing me to Access Victim Accounts Without 2FA Code
Author: Amine SAJID
Introduction
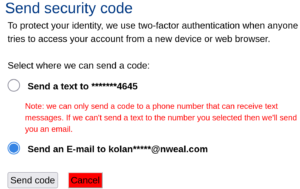
During a security assessment of a public program, I discovered a 2FA bypass bug that allows attackers to bypass the two-factor authentication (2FA) mechanism by using the mobile application. This vulnerability allows attackers to login to their accounts without requiring a 2FA code, leading to unauthorized access.
Bug Type: 2FA Bypass Bug
Impact: Unauthorized Account Access, Security Bypass
Severity: Medium
The Hunt Begins
After logging in, I was prompted for a 2FA code to access my account. I tried several techniques to bypass the 2FA, such as:
- Entering
000000as the code. - Checking if the 2FA code was leaked in the response.
- Testing if another user’s 2FA code would work.
- Attempting to access dashboard endpoints without entering the 2FA code…
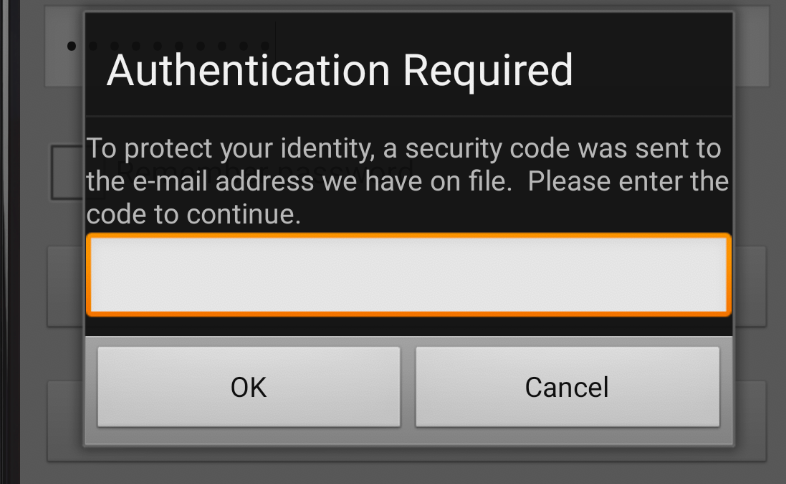
Unfortunately, none of these methods worked. I was confident that the 2FA implementation had a vulnerability, and I suddenly remembered that this program also had a mobile application. This time, instead of focusing on the web application, I decided to shift my attention to the mobile app.
To my surprise, when I logged in through the mobile app, I was not prompted for a 2FA code at all. The authentication process on the mobile app seemed to skip the 2FA step entirely, allowing me to access my account seamlessly. granting me access to the account without needing to enter any additional verification code.
The program fixed the issue, but I was able to bypass it again. Read How
Impact
Unauthorized Access: Attackers can easily login to their accounts without the need for a 2FA code.
Recommended Fix
Require 2FA For The Mobile App: Ensure that the mobile application also requires 2FA verification before allowing users to login.
Conclusion
This 2FA bypass vulnerability highlights a major weakness in the authentication process. While two-factor authentication (2FA) is meant to add an extra layer of security, this flaw completely bypasses it, putting user accounts at risk of unauthorized access.
Final Thoughts:
Hacking and bug bounty hunting aren’t always about using complex codes and payloads. Sometimes, all you need is a hacker’s mindset to creatively exploit the features built by developers.